Cloud Workload
Network Activities
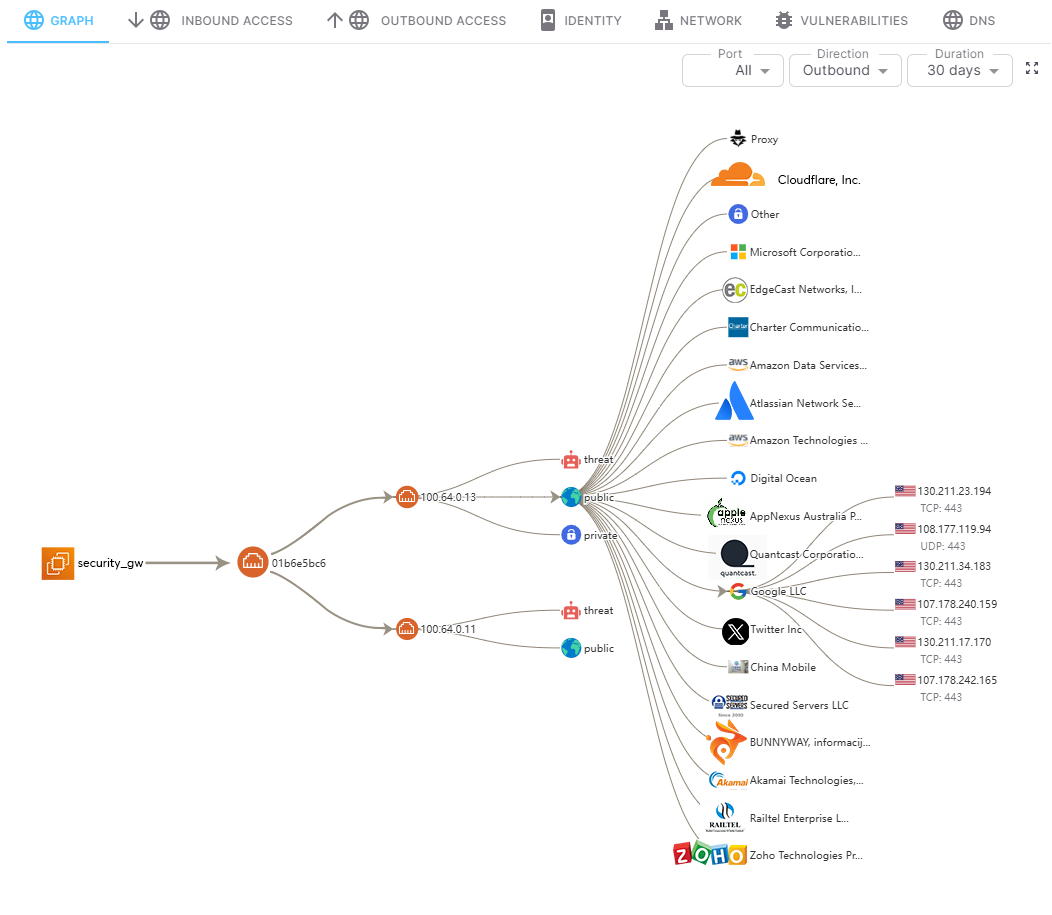
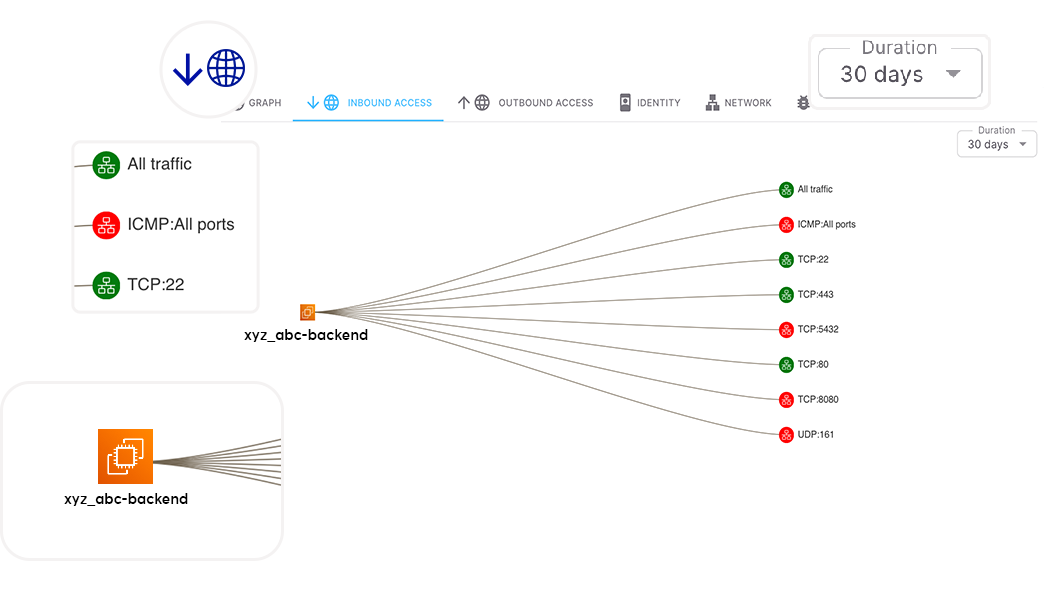
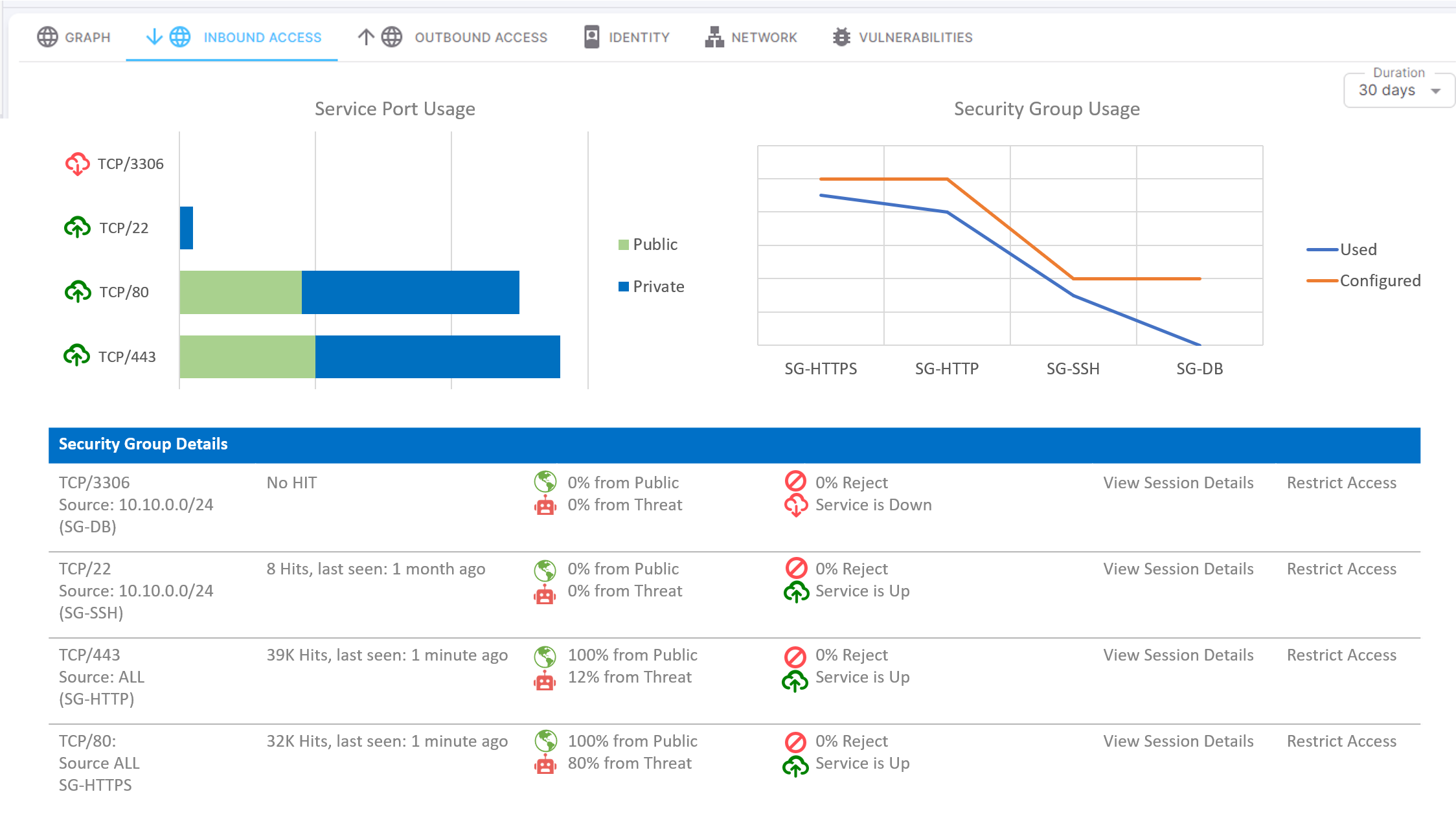
We continuously monitor the network communications and activities of every cloud workload, by collecting vpc flow logs, DNS logs,...etc and provide extensive visibility.
We establish behavioral baselines for each workload to identify deviations and suspicious activities, and prevent attacks before they escalate. We cross check every communication with security group configuration to spot and remove unused access.

Cloud Workload
Identities
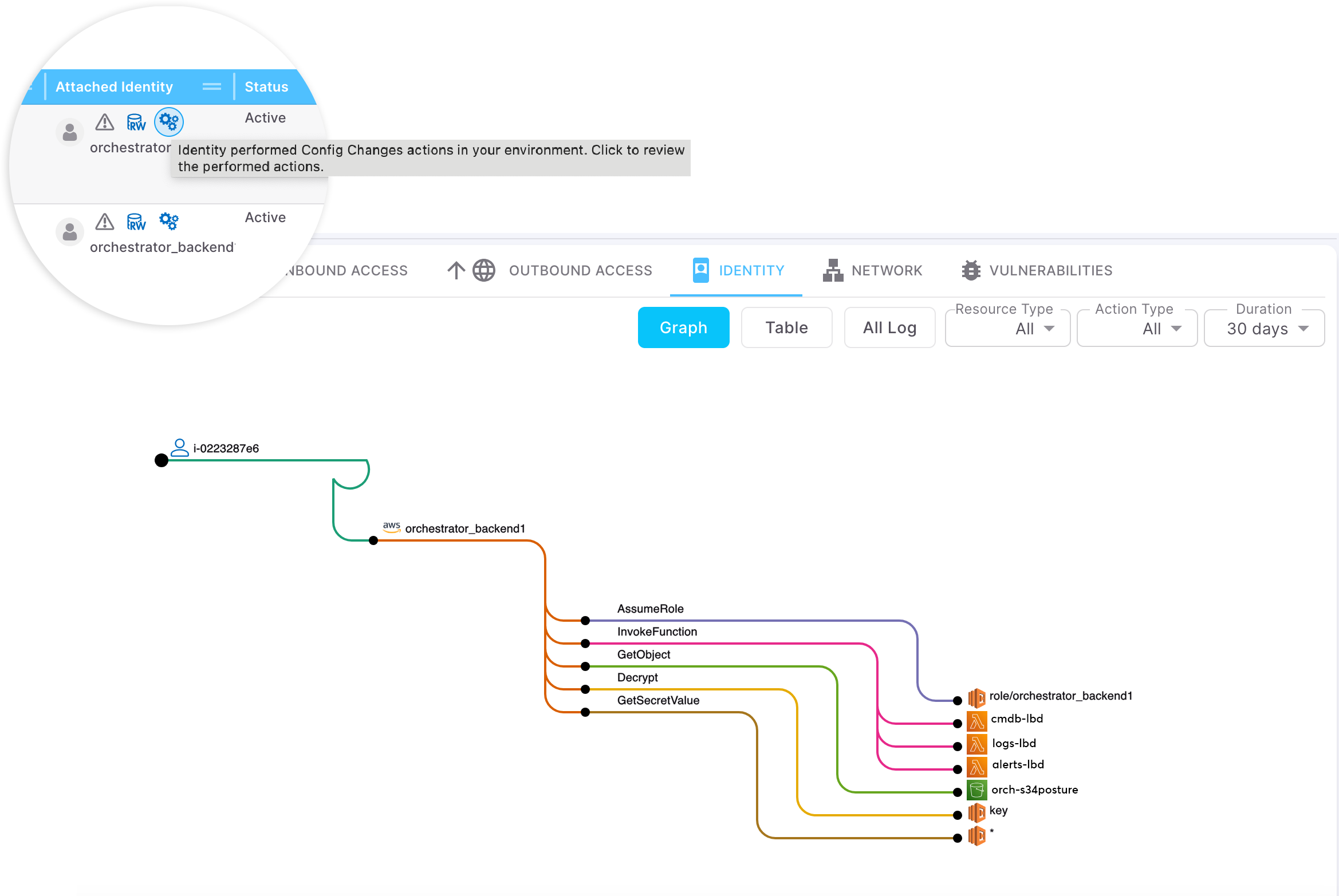
Cloud Workload activities isn't just about the network traffic; it is also about identity activities
For every workload identity, we monitor its activities and build its behavior baseline, making it very easy for Security and DevOps teams to apply least privilege policies and swiftly detect behavior changes or suspicious activities.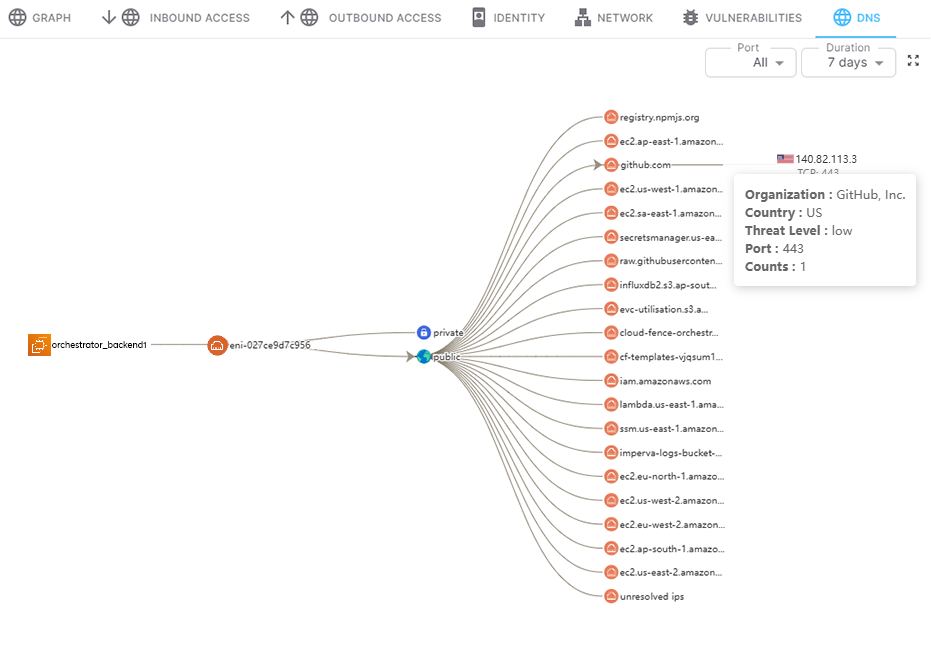
 You want to restrict the outbound access to specific destinations,
but do you know the destinations and services your workload needs to communicate with?
You want to restrict the outbound access to specific destinations,
but do you know the destinations and services your workload needs to communicate with?